authority management#
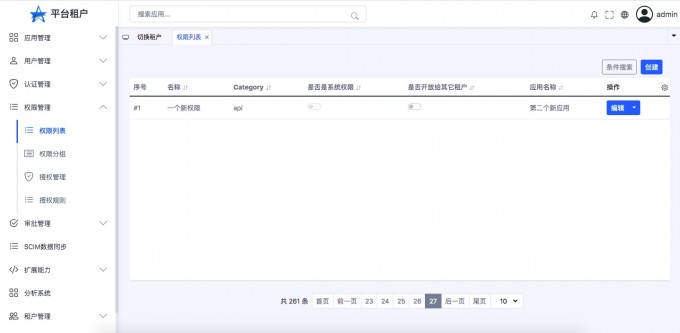
Permission list#
View the permissions information that can be read by the login user,New and editing permissions, etc.
- "Open permission list"
- "New authority"
- "View creation results"
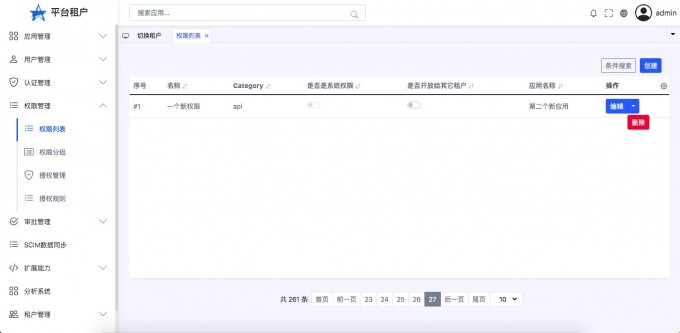
- "Delete permissions"
Only the permissions created by yourself are allowed to delete,Can't delete system permissions
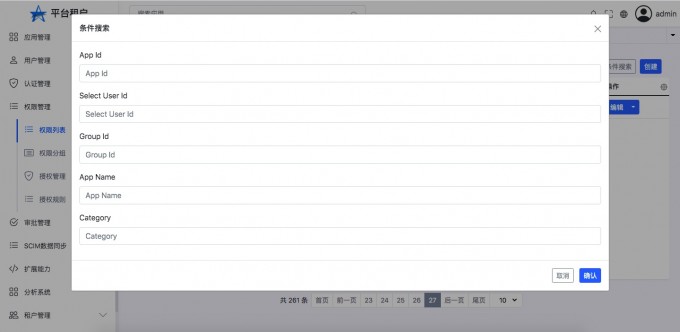
- "Permission search"
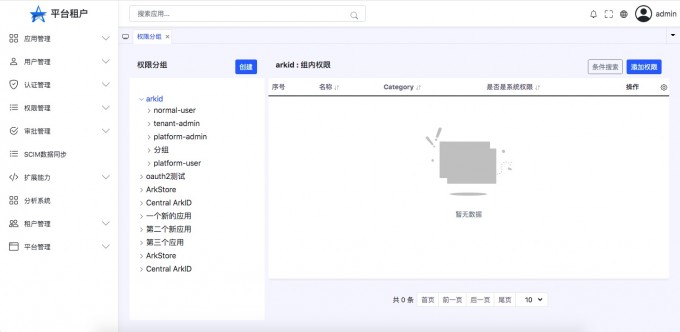
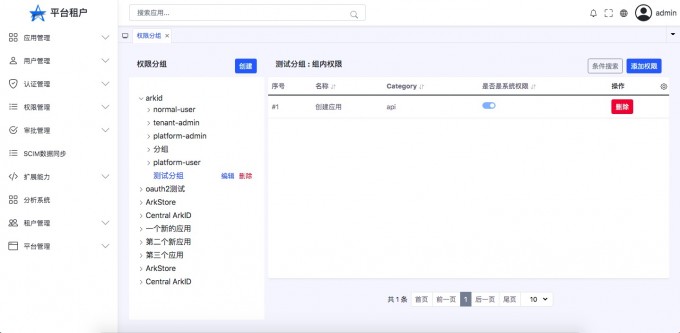
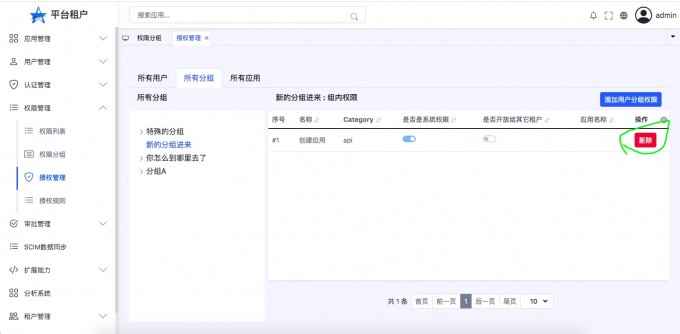
Permissions#
The left tree structure,The first layer is the application,The second layer is a group of permissions in the application。
On the right is the permissions in the grouping
You can create a new permissions group here again,And edit the authority。
- "Open the List of Permanent Subsidies"
- "New authority group"
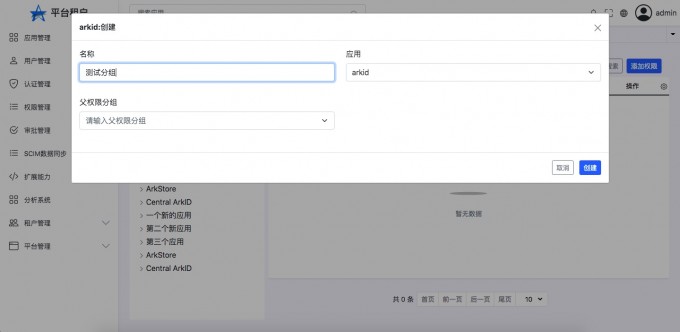
- "View creation results"
Only the permissions group created by yourself allow delete and editing,Can't delete and edit system groups
- "View permissions of permission grouping"
- "Power packet adding permissions"
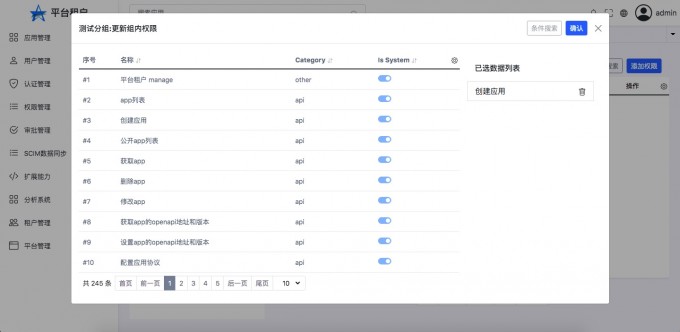
- "View the result of adding permissions"
Only the permissions added by yourself can be deleted
Authorization#
From three perspectives:user,User group,application To allocate permissions
Can add permissions or delete permissions to a user
You can add permissions or delete permissions to a user
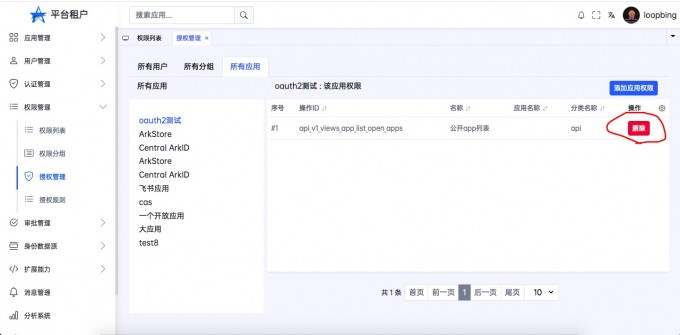
You can add permissions or delete permissions or open permissions to an application
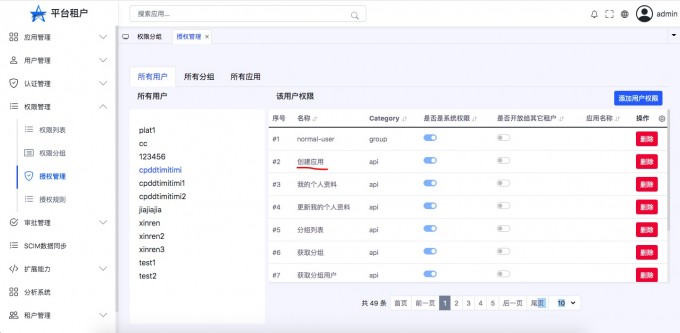
User rights#
- "Open the user authority list"
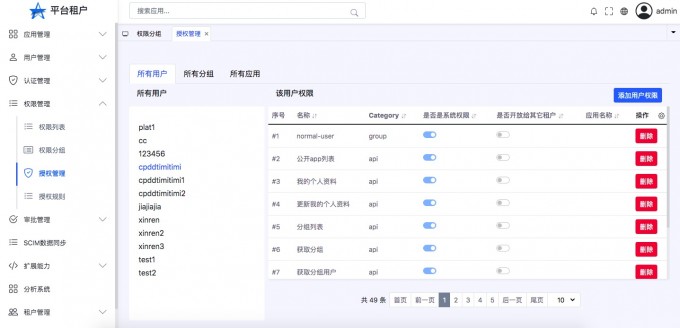
- "Add user permissions"
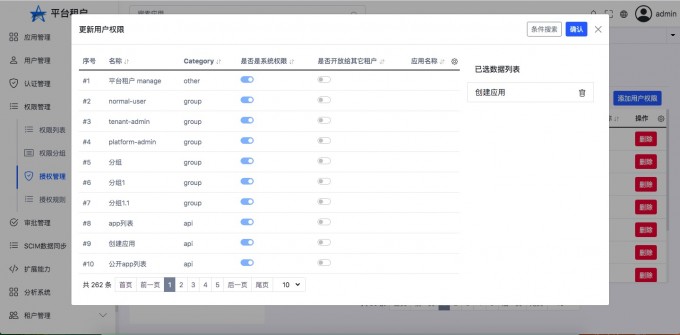
- "View the result of adding permissions"
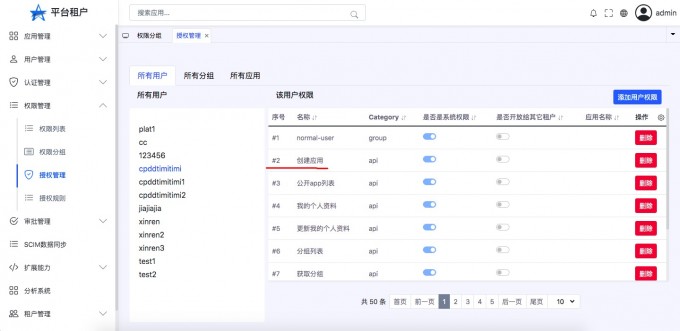
- "Delete user permissions"
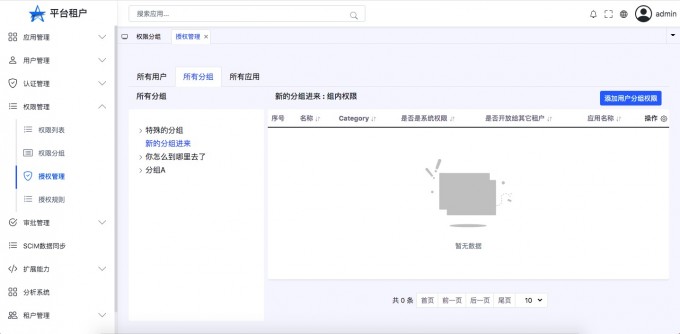
User packet authority#
- "Open the user group list"
- "Add user group permissions"
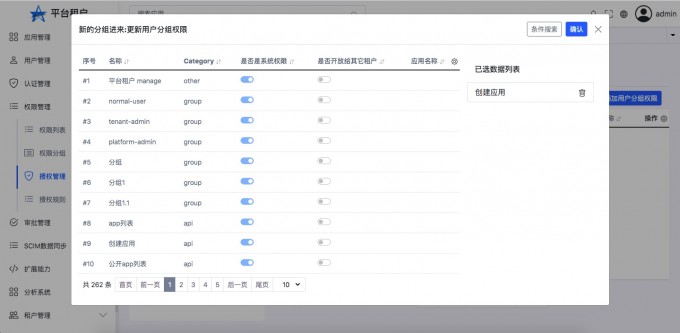
- "View the user's grouping permissions"
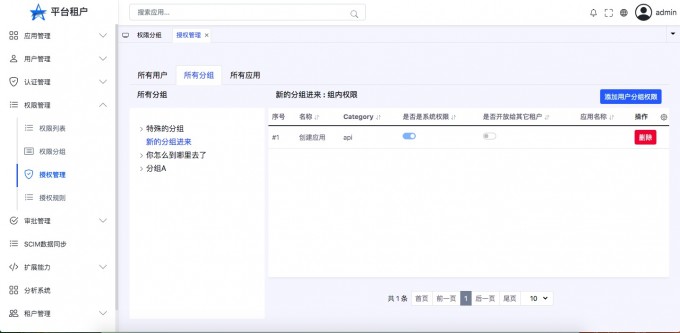
- "Delete user group permissions"
Application authority#
- "Open the application right list"
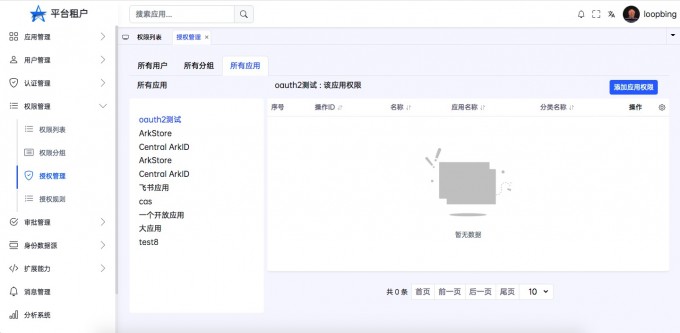
- "Add application permissions"
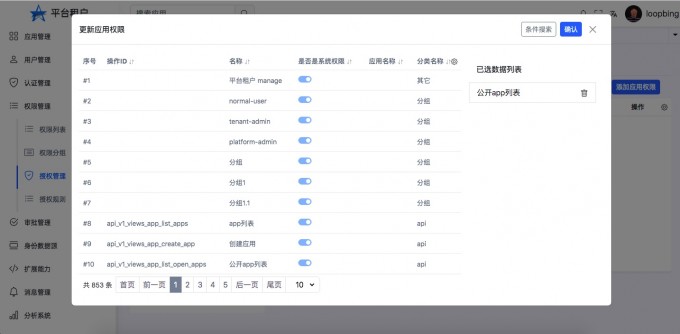
- "View the application permissions added"
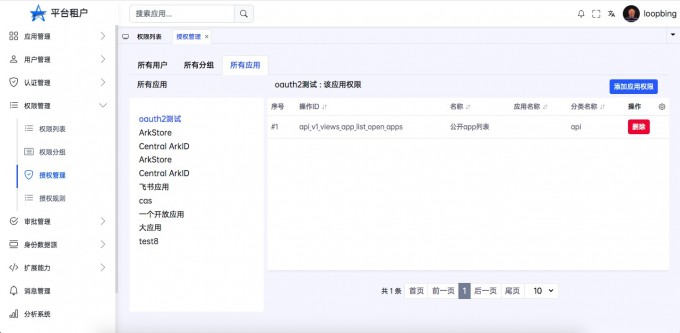
- "Delete application permissions"
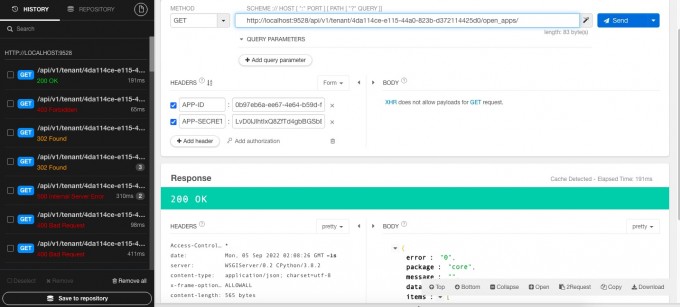
If you use the application ID and secret access#
-
"Access with application ID and secret,You need to add an app to Headers-ID and app-Secret parameter"
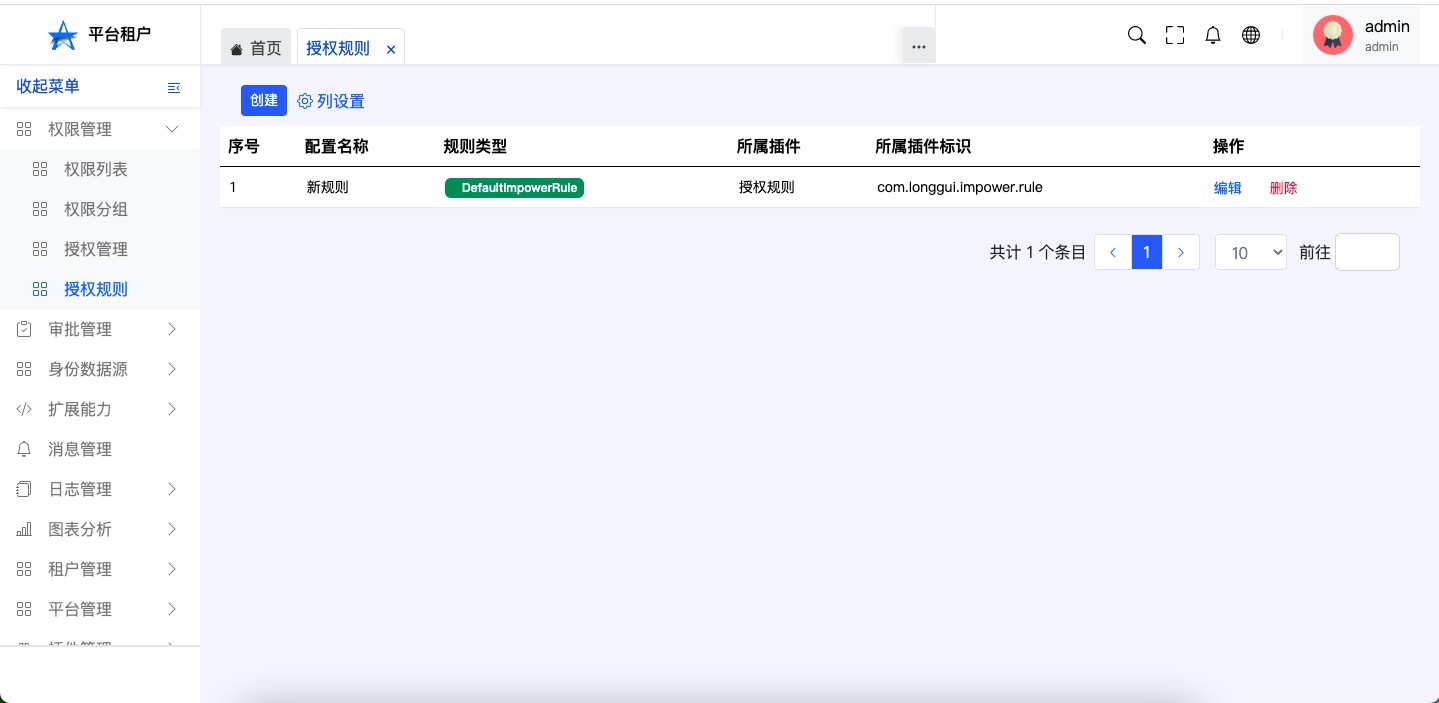
Authorization rules#
In addition to the authorization management method of RBAC in authorization management,And ABAC's authority management method。The authorization rules are used to handle the type of ABAC。
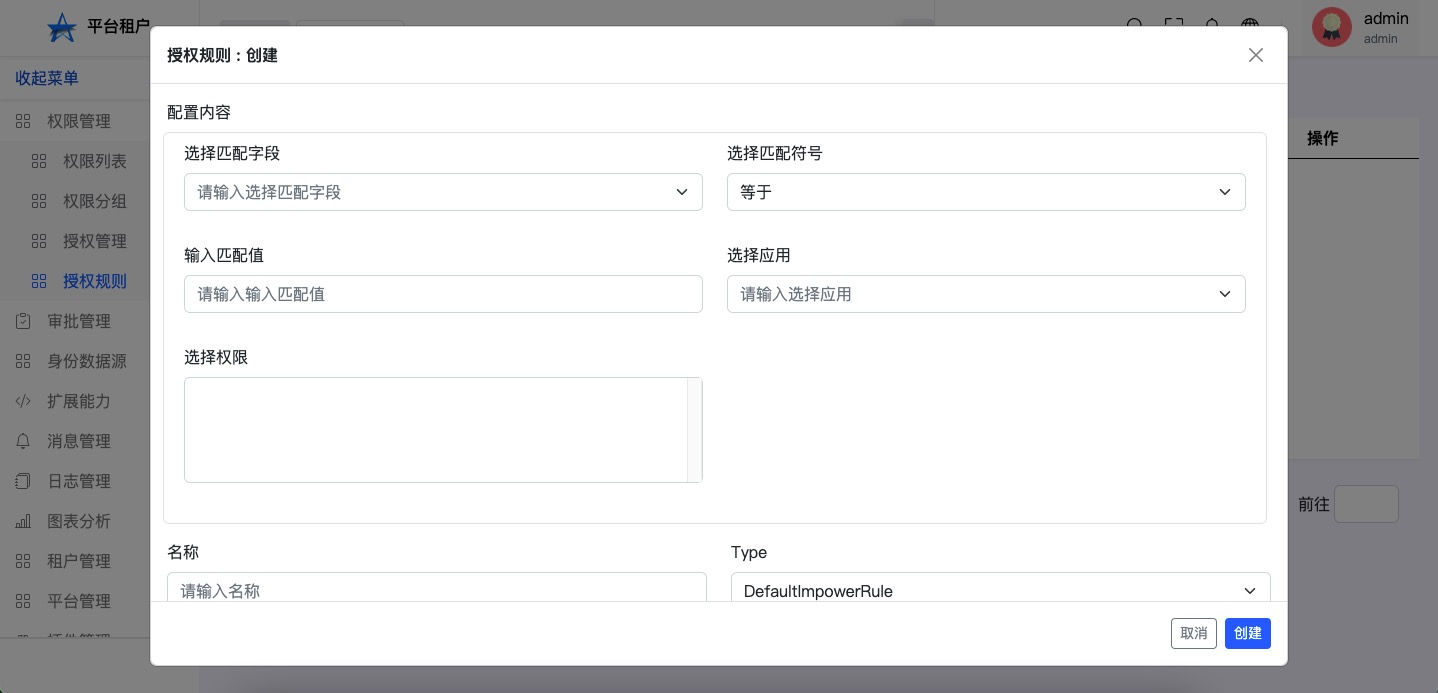
Click to create,You can add the relevant plug -in configuration。
Different plug -in processing authorization rules are different,The respective configuration is also different,Please refer to [Detailed plug -in document] (../../../../%20%20 system plug -in/com_Dragon turtle_impower_rule/DefaultImpowerRule/)
- "Open the list of authorization rules"
- "Newly -built authorization rules"
- "Edit Authorization Rules"
- "Delete authorization rules"